Cloud-based software and tools are the present, not the future, of business. By storing information and applications running on distant servers that are reachable from any location with an internet..
Are you looking to disconnect the link between Microsoft and Google accounts? Whether you previously connected Outlook with Gmail, synced Microsoft To Do with Google Calendar, or linked Office 365..
In today’s hyper-connected digital economy, cloud computing is no longer optional it is foundational. Businesses across industries rely on scalable, secure, and intelligent platforms to drive innovation and maintain competitive..
The Tool Everyone Has But Nobody LovesMicrosoft Teams is one of the most widely deployed collaboration platforms in the world. It ships bundled with Microsoft 365, which means millions of..
The real estate and multifamily industry is becoming more data-driven every year. Property managers are no longer just handling leases and maintenance; they are managing finances, customer relationships, compliance, and..
In an era dominated by advanced analytics platforms, AI-driven tools, and cloud-based systems, Microsoft Excel might seem like a relic from the past. Yet, despite the rapid evolution of technology,..
In today’s rapidly evolving digital landscape, businesses must embrace scalable, secure, and innovative technologies to stay competitive. MicroSoft Azure Training in Hyderabad has emerged as a pivotal force, enabling organizations..
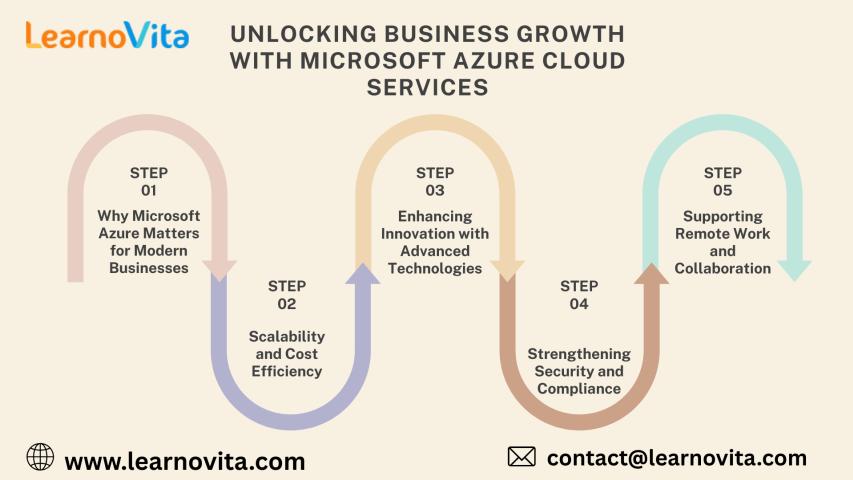
In today’s fast-paced digital economy, businesses must be agile, scalable, and data-driven to stay competitive. Cloud computing has become a cornerstone of modern enterprise strategy, and Microsoft Azure stands out..
Losing access to MDB & ACCDB files due to forgotten password can lead to interrupt the workflow. Since MS Access database stores important information and it requires password protection. But..
If you find yourself steering a Google
Workspace–to–Microsoft 365 migration, it’s common to feel overwhelmed by
the labyrinth of configuration steps. Many administrators face the same
uncertainty, which is why..
As
a constantly changing topic of cybersecurity, endpoint defense (laptops,
desktops, servers, and mobile devices) has never been more important. Cyber
threats are getting advanced, and hence, the antivirus systems..
As the world becomes increasingly digital, network security takes center stage in protecting organizations from emerging threats. CCIE Security certification plays a pivotal role in equipping professionals with the skills..
Introduction: Why Encryption Matters in Today’s Digital WorldImagine sending a message that only the intended recipient can read, even if someone else intercepts it. That’s the power of encryption. With..
Introduction: Why Firewalls Are the First Line of Defense in Cyber SecurityIn today’s hyperconnected world, cyber threats are growing in scale and complexity. Every business, small or large, faces the..
In today's fast-moving digital world, the terms Artificial Intelligence (AI) and Machine Learning (ML) are everywhere. Whether it's a self-driving car navigating traffic or a voice assistant scheduling meetings, these..
In the rapidly evolving world of digital marketing, data analytics has become an essential tool for marketers seeking to optimize their campaigns. By harnessing the power of data, businesses can..
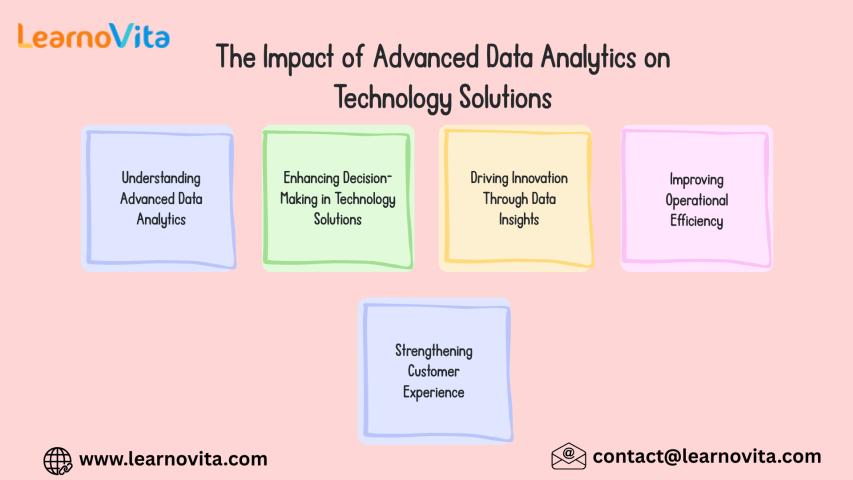
In today’s digital era, data has become one of the most valuable assets for businesses and organizations. With the rapid growth of digital technologies, companies generate enormous volumes of data..
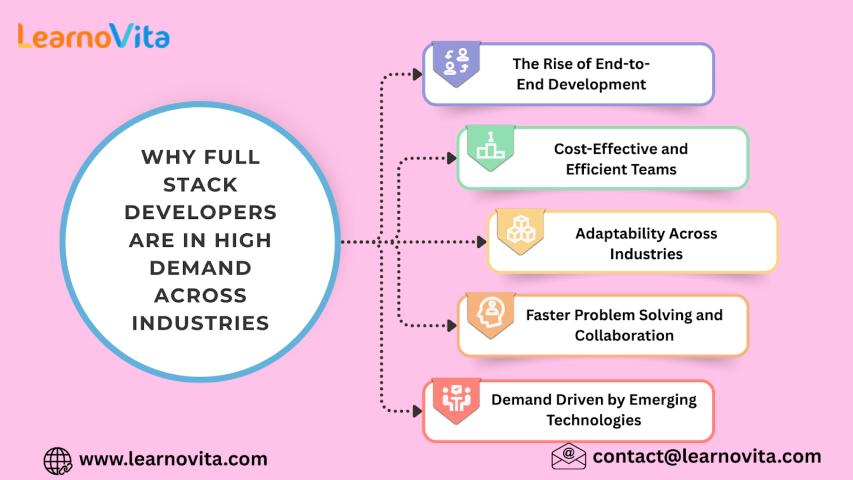
In today’s fast-paced digital economy, businesses across industries are racing to build scalable, user-friendly, and high-performing applications. From startups to global enterprises, organizations are prioritizing agility and innovation. This growing..