Insider threats remain one of the most challenging security risks for tech organizations. Unlike external attacks, insider incidents can originate from trusted users employees, contractors, vendors, or even compromised accounts with legitimate access. Whether intentional or accidental, these threats can lead to data breaches, service disruptions, and reputational damage. CyberArk Training in Hyderabad addresses this risk by focusing on protecting privileged access, strengthening identity security, and enforcing controls that reduce the chances of misuse across the enterprise.
CyberArk’s Approach to Minimizing Insider Threats in Tech Organizations
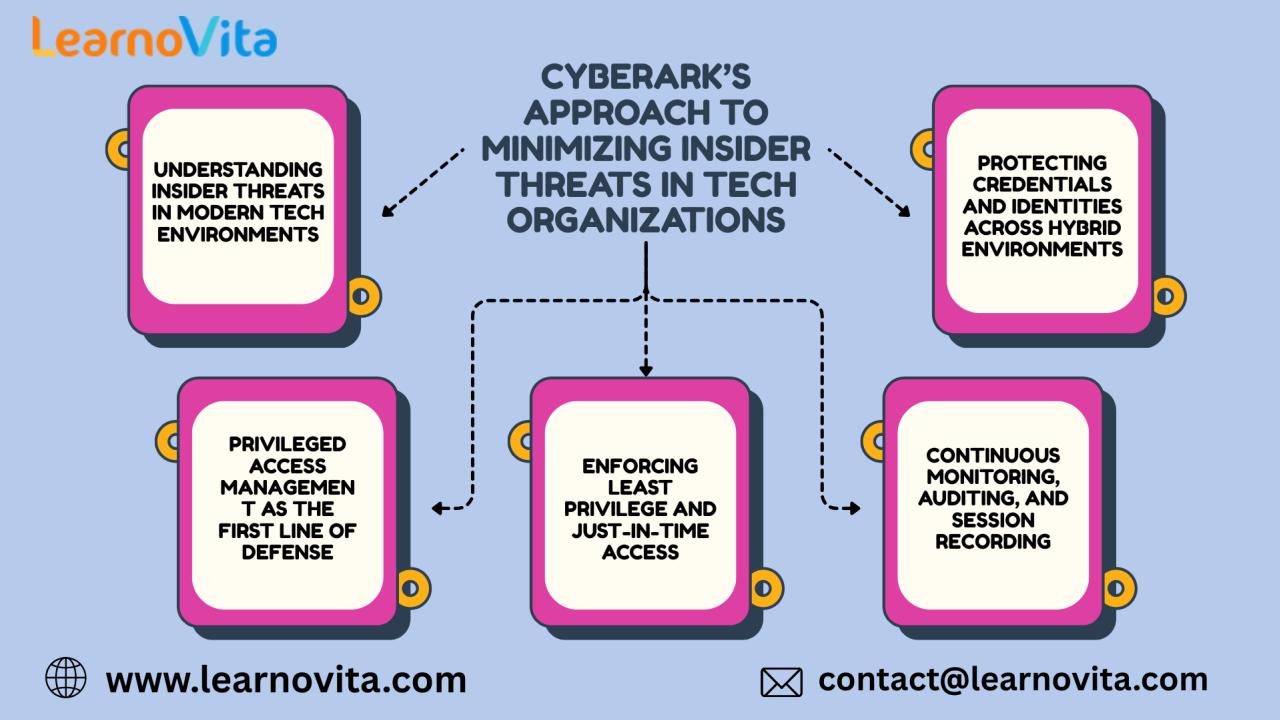
Image credits: CyberArk’s Approach to Minimizing Insider Threats in Tech Organizations
Written by
rajaganapathi114
4 days ago
Related articles:
Basics of Encryption and Decryption
Introduction: Why Encryption Matters in Today’s Digital WorldImagine sending a message that only the intended recipient can read, even if someone else intercepts it. That’s the power of encryption. With..
Importance of Firewalls in Cyber Security
Introduction: Why Firewalls Are the First Line of Defense in Cyber SecurityIn today’s hyperconnected world, cyber threats are growing in scale and complexity. Every business, small or large, faces the..
What Is the Difference Between Artificial Intelligence and Machine Learning?
In today's fast-moving digital world, the terms Artificial Intelligence (AI) and Machine Learning (ML) are everywhere. Whether it's a self-driving car navigating traffic or a voice assistant scheduling meetings, these..
How to Use Data Analytics to Optimize Your Marketing Campaigns
In the rapidly evolving world of digital marketing, data analytics has become an essential tool for marketers seeking to optimize their campaigns. By harnessing the power of data, businesses can..
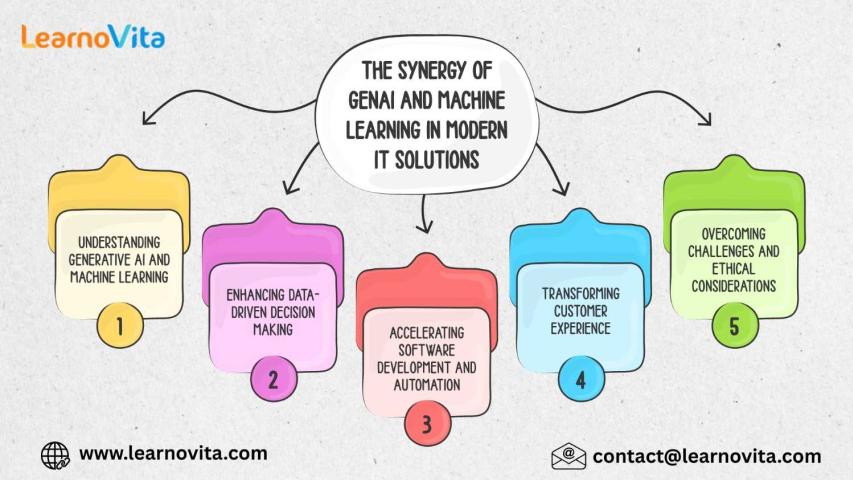
The Synergy of GenAI and Machine Learning in Modern IT Solutions
In today’s fast-paced digital landscape, businesses constantly seek innovative ways to optimize operations, enhance customer experiences, and stay ahead of competitors. One of the most transformative trends in modern IT..
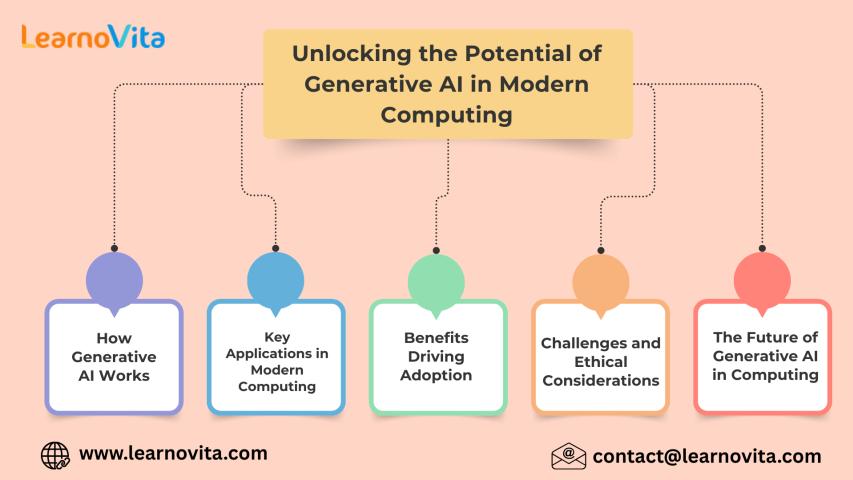
Unlocking the Potential of Generative AI in Modern Computing
Generative Artificial Intelligence (AI) is transforming modern computing by enabling machines to create content, designs, code, and insights that closely resemble human output. Unlike traditional AI systems that rely on..
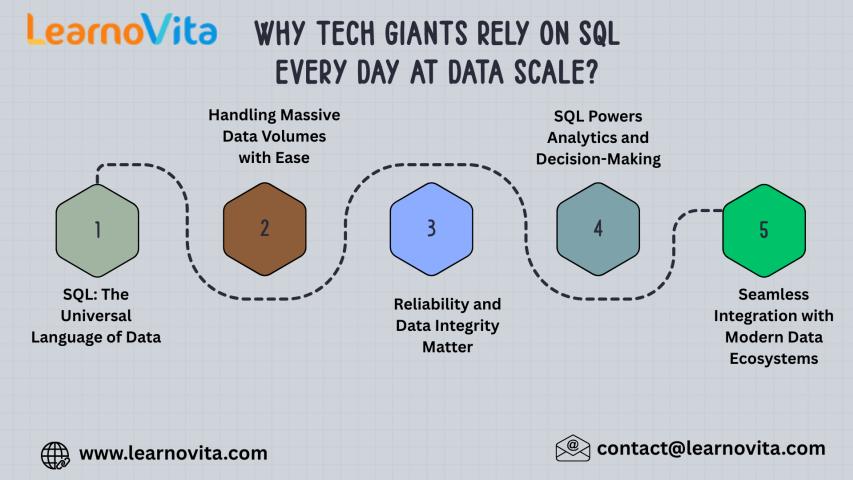
Why Tech Giants Rely on SQL Every Day at Data Scale?
In an era dominated by artificial intelligence, real-time analytics, and massive cloud infrastructures, one technology continues to quietly power the world’s largest companies: SQL. Despite the rise of NoSQL databases..
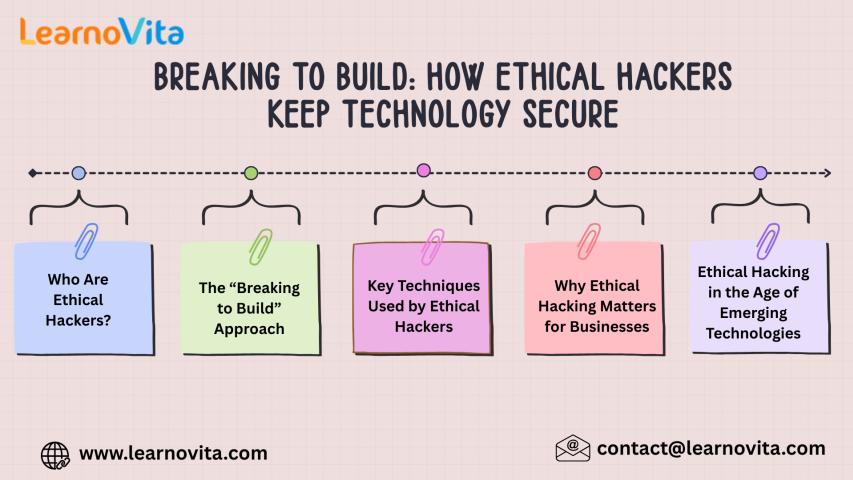
Breaking to Build: How Ethical Hackers Keep Technology Secure
In an increasingly digital world, cybersecurity threats are evolving faster than ever. From data breaches to ransomware attacks, organizations face constant risks to their systems and sensitive information. This is..
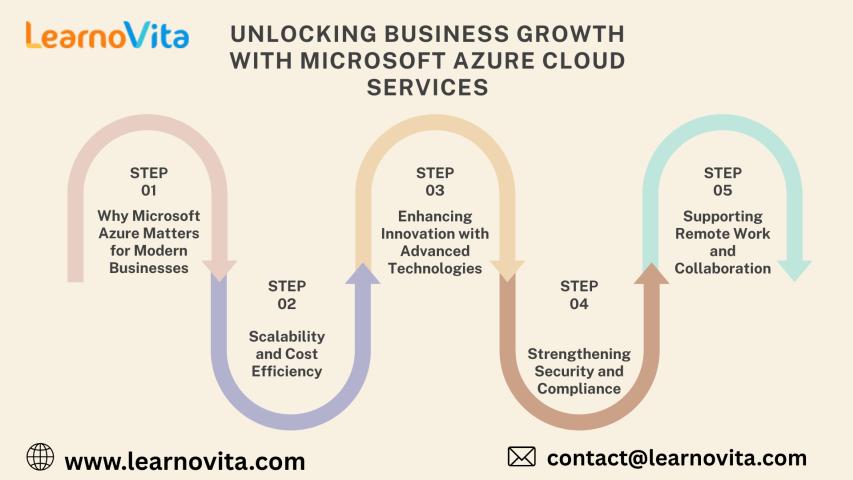
Unlocking Business Growth with Microsoft Azure Cloud Services
In today’s fast-paced digital economy, businesses must be agile, scalable, and data-driven to stay competitive. Cloud computing has become a cornerstone of modern enterprise strategy, and Microsoft Azure stands out..
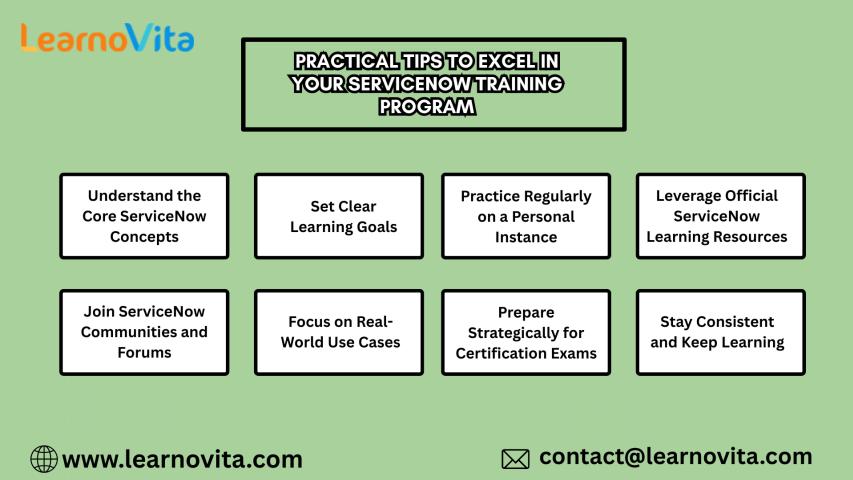
Practical Tips to Excel in Your ServiceNow Training Program
ServiceNow has become a cornerstone platform for digital workflows, IT service management, and enterprise automation. Whether you are a beginner exploring the basics or a professional aiming for certification, excelling..